Information Security for Researchers (and Journalists)

Our information processing tools are an interconnected system: what can an investigative researcher do in order to secure data or protect sources? The TCIJ’s handbook has a few good tips.
The handbook on Information Security for Journalists, by Silkie Carlo and Arjen Kamphuis, recently published by The Centre for Investigative Journalism (http://www.tcij.org/node/1016) is an important reference for post-Snowden era journalists and investigative reporters. The revelations of massive untargeted surveillance by the NSA, and the increased sophistication of targeted information break-ins have heightened risk perceptions among many practitioners dealing with sensitive information and sources. Researchers conducting fieldwork in troubled hotspots on issues slightly more mundane than courtly ghazal poetry have many reasons to see themselves as part of the target audience as well.
The Snowden papers showed that every electronic communication we make or receive is being recorded, stored and subject to analysis. The NSA bugaboo – but we should not discount other state and corporate big brothers – conduct their surveillance in secret, hardly leaving any trace, without judicial scrutiny worth the name. If the homemade arsenal available to government agencies is not up to the task they can always shop around for fancy kit, ‘offensive technology’ produced by specialized companies like the Milan-based Hacking Team.
So what can an investigative researcher do in order to secure his/her data or protect sources against these formidable odds? The TCIJ’s handbook has a few good tips for them, starting from the basics: think of your information processing tools as an interconnected system. If one part is compromised, the whole will be compromised. One has to pay attention to the process, not only to the individual parts. A critical uncompromising look over all kit, starting from the hardware, will bring Apple aficionados some unpleasant news: Macbooks get a thumb down from the authors, unless for very low risk security situations. The main reasons: the are not open enough – and we’re still talking about hardware – for internal inspection against potential tampering and for substituting or eliminating vulnerable components, like microphone, webcam, bluetooth or wifi module. From this example we can see that the authors take the issue seriously. The handbooks of course covers also software choices and practices.
While encouraging the readers to have a serious look at this useful handbook, I want to add a couple of tips. The first is about the mental universe of the geeky spooks that are trying so hard to stick their fingers in our jealously guarded data. As the old adage of spy-story lore had it, if you want to guard yourself from an enemy, start thinking as they do. A very good starting point – meaning high quality written stuff – in this regard is Neal Stephenson’s classic, Cryptonomicon.
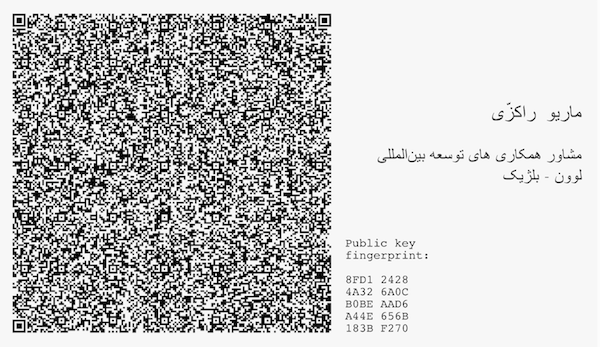
The second tip is more technical, combining high and low, digital and analog tech. The software suite of choice for email encryption recommended by the handbook is GPG, a popular open source implementation of Pretty Good Privacy (PGP) developed by Phil Zimmerman in the early 1990s. Long story short, in order for PGP to work the user has two keys (rather long sequences of bits): a private one that he will keep very very secret without sharing it with anyone, not even mom or most significant other. The second is the public key that on the contrary will have to be disseminated among her correspondents. If Alice uses Bob’s public key to encrypt a message, the only way to decrypt the message is to use Bob’s private key. So far so good. Things gets murkier if Mallory somehow provides Alice with a key that is not Bob’s, but persuading her that this is the case. If Alice uses the bad key it will be easy for Mallory to intercept the message, decrypt and store it, while at the same time sending Bob the message but this time encrypted with Bob’s public key. So public key management is critical for PGP and current practices of public key repositories or indirect webs of trust are far from being bulletproof. The following tip is no panacea but can make a researcher’s life easier in those situation – quite common during fieldwork – when she meets her sources in person. In these meetings the most straightforward way to exchange keys is to have the public key directly printed on the back of the business card as a QR matrix (the key itself is too long for being reproduced) that can be easily read by the average smartphone. Adding a key fingerprint give the correspondent an easy way to check if the public key that she had downloaded from and online repository matches the actual one used by the researcher.
Originally published on Security Praxis
Cover image credit: GoatChild, Street Art by SpY in Madrid (CC-BY-SA)